Confidential Computing in a nutshell
🌰 Confidential Computing in a nutshell: 🌰
Don’t trust the cloud, trust the hardware manufacturer.
But can you trust the hardware manufacturer?
Confidential Computing in a Nutshell. Source
Context and Problem
🚩 The problem: Several court rulings made it clear that GDPR is incompatible with US cloud providers due to “official access channels”.
✨ The solution: “Just use encryption!”
⛔ Next problem: Does the US cloud have access to decryption keys? Could they decipher the data, if asked via “official channels”?
✨ The solution: Make it technically impossible for the cloud provider to decipher the data.
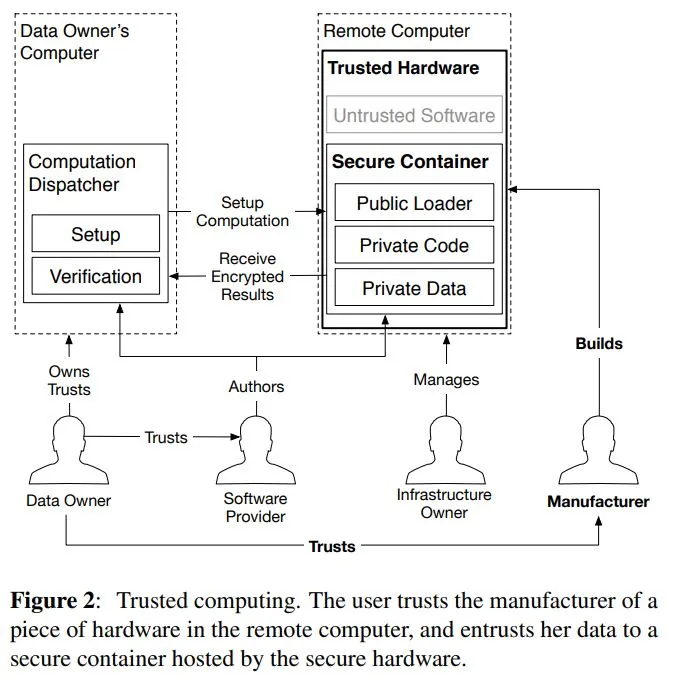
How does confidential computing work?
I’m a bit over-simplifying, but here is “jargon-removed-but-still-kinda-accurate” technical description of Confidential Computing:
- The CPU enforces separation. Application code and data (i.e., containers or VMs) runs in so-called “enclaves”. The CPU makes sure that “cloud provider code and data” (i.e., hypervisor) cannot access code and data in enclaves.
- The CPU provides attestation. It proves to the application developer (via code hashing and public cryptography) that the developer truly talks to their code and that the code truly runs in an enclave.
- The CPU stores the keys, both for encryption and attestation. The CPU pinky promisses to not have a security bug or backdoor to release the keys.
So, should we trust Confidential Computing? https://eprint.iacr.org/2016/086.pdf said this:
[O]ur security analysis reveals that the limitations in SGX’s [CPU instructions needed for Confidential Computing] guarantees mean that a security conscious software developer cannot in good conscience rely on SGX for secure remote computation.
For anyone dying to read 118 pages to get all the details behind SGX, the current technology fueling Confidential Computing, here is an article from MIT: https://eprint.iacr.org/2016/086.pdf
Conclusion
🤔 Personally, I’m unsure. Is Confidential Computing finally the incarnation of trusted computing we’ve all been waiting for? Or is it yet another “just use encryption” argument post-Schrems2?
What do you think?
Please join the conversation by leaving a comment on this LinkedIn post.